An official FBI document dated January 2021, obtained by the American association "Property of People" through the Freedom of Information Act.
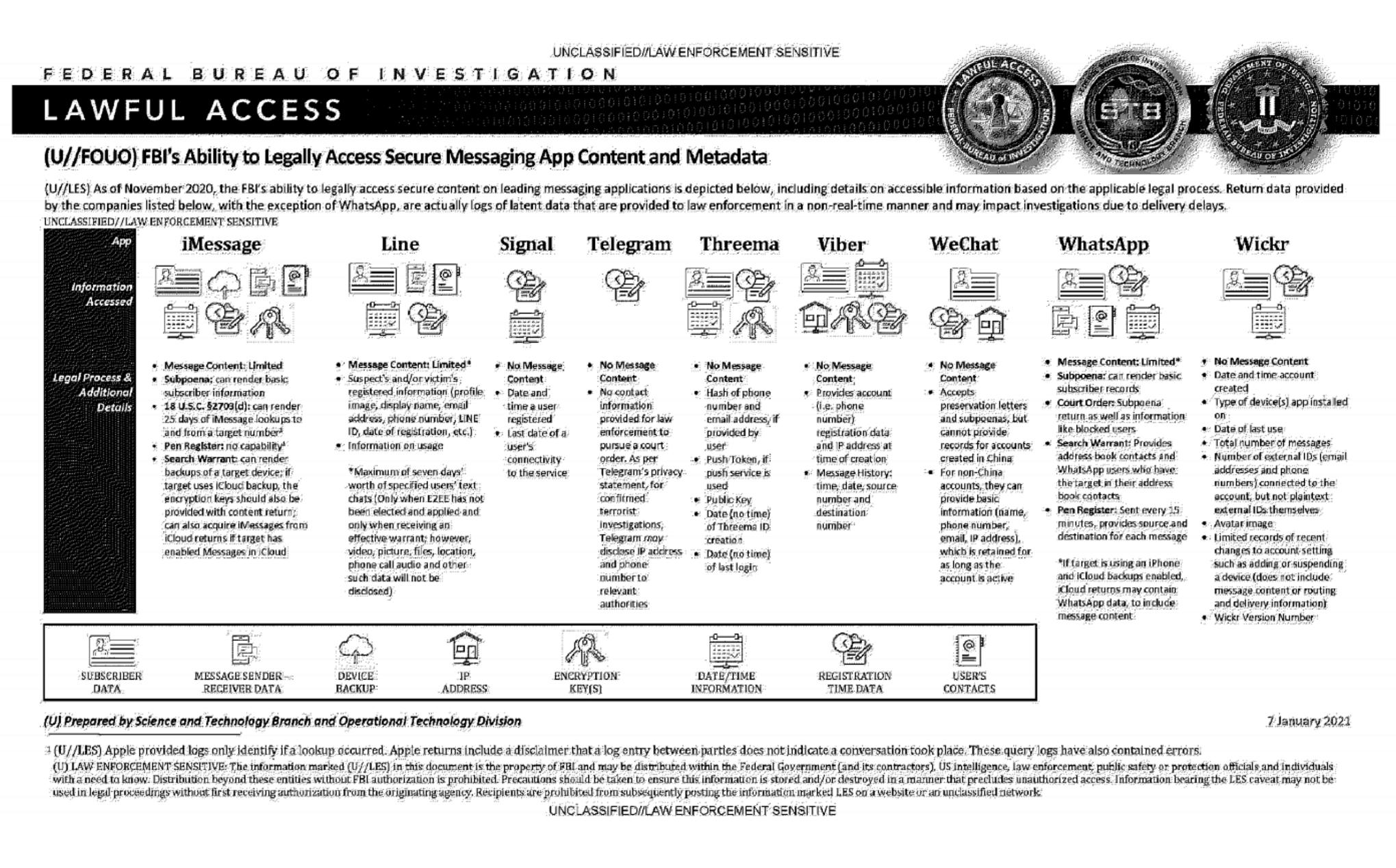
This document summarizes the possibilities for legal access to data from nine instant messaging services: iMessage, Line, Signal, Telegram, Threema, Viber, WeChat, WhatsApp and Wickr. For each software, different judicial methods are explored, such as subpoena, search warrant, active collection of communications metadata ("Pen Register") or connection data retention law ("18 USC§2703"). Here, in essence, is the information the FBI says it can retrieve:
-
Apple iMessage: basic subscriber data; in the case of an iPhone user, investigators may be able to get their hands on message content if the user uses iCloud to synchronize iMessage messages or to back up data on their phone.
-
Line: account data (image, username, e-mail address, phone number, Line ID, creation date, usage data, etc.); if the user has not activated end-to-end encryption, investigators can retrieve the texts of exchanges over a seven-day period, but not other data (audio, video, images, location).
-
Signal: date and time of account creation and date of last connection.
-
Telegram: IP address and phone number for investigations into confirmed terrorists, otherwise nothing.
-
Threema: cryptographic fingerprint of phone number and e-mail address, push service tokens if used, public key, account creation date, last connection date.
-
Viber: account data and IP address used to create the account; investigators can also access message history (date, time, source, destination).
-
WeChat: basic data such as name, phone number, e-mail and IP address, but only for non-Chinese users.
-
WhatsApp: the targeted person's basic data, address book and contacts who have the targeted person in their address book; it is possible to collect message metadata in real time ("Pen Register"); message content can be retrieved via iCloud backups.
-
Wickr: Date and time of account creation, types of terminal on which the application is installed, date of last connection, number of messages exchanged, external identifiers associated with the account (e-mail addresses, telephone numbers), avatar image, data linked to adding or deleting.
TL;DR Signal is the messaging system that provides the least information to investigators.