46
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
this post was submitted on 11 Nov 2024
46 points (100.0% liked)
technology
23313 readers
73 users here now
On the road to fully automated luxury gay space communism.
Spreading Linux propaganda since 2020
- Ways to run Microsoft/Adobe and more on Linux
- The Ultimate FOSS Guide For Android
- Great libre software on Windows
- Hey you, the lib still using Chrome. Read this post!
Rules:
- 1. Obviously abide by the sitewide code of conduct. Bigotry will be met with an immediate ban
- 2. This community is about technology. Offtopic is permitted as long as it is kept in the comment sections
- 3. Although this is not /c/libre, FOSS related posting is tolerated, and even welcome in the case of effort posts
- 4. We believe technology should be liberating. As such, avoid promoting proprietary and/or bourgeois technology
- 5. Explanatory posts to correct the potential mistakes a comrade made in a post of their own are allowed, as long as they remain respectful
- 6. No crypto (Bitcoin, NFT, etc.) speculation, unless it is purely informative and not too cringe
- 7. Absolutely no tech bro shit. If you have a good opinion of Silicon Valley billionaires please manifest yourself so we can ban you.
founded 4 years ago
MODERATORS
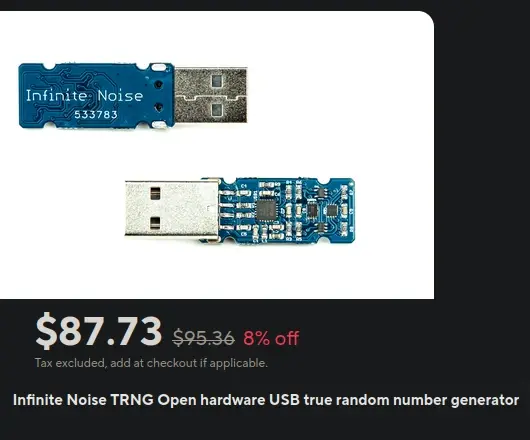
Yeah, not USB but in principle it's the same whether it's PCI or whatever. There's no way to prove an RNG is truly random really just have to rely on validating subsets of its output look random. NIST has published recommendations for sampling RNGs.
Here's the title:
I don't think there's a real need unless it's regulated to need some dedicated HW RNG.
Very precise answer, thank you.
How about a simple test to make sure it didn't break and start spitting out all zeroes. Read a few lines from
/dev/random?I might be wrong about this but my understanding is that on Linux you'd pipe the output of this in somewhere and tell the kernel to use it for entropy, and if it gets insufficient entropy it realizes this and starts producing random bits slower. So like normally the Linux kernel samples mouse movements for randomness, and so it makes more random bits the more you jiggle your mouse. These hardware RNGs are best used for headless servers that don't have as reliable entropy at their disposal.