view the rest of the comments
Games

Welcome to the largest gaming community on Lemmy! Discussion for all kinds of games. Video games, tabletop games, card games etc.
Rules
1. Submissions have to be related to games
Video games, tabletop, or otherwise. Posts not related to games will be deleted.
This community is focused on games, of all kinds. Any news item or discussion should be related to gaming in some way.
2. No bigotry or harassment, be civil
No bigotry, hardline stance. Try not to get too heated when entering into a discussion or debate.
We are here to talk and discuss about one of our passions, not fight or be exposed to hate. Posts or responses that are hateful will be deleted to keep the atmosphere good. If repeatedly violated, not only will the comment be deleted but a ban will be handed out as well. We judge each case individually.
3. No excessive self-promotion
Try to keep it to 10% self-promotion / 90% other stuff in your post history.
This is to prevent people from posting for the sole purpose of promoting their own website or social media account.
4. Stay on-topic; no memes, funny videos, giveaways, reposts, or low-effort posts
This community is mostly for discussion and news. Remember to search for the thing you're submitting before posting to see if it's already been posted.
We want to keep the quality of posts high. Therefore, memes, funny videos, low-effort posts and reposts are not allowed. We prohibit giveaways because we cannot be sure that the person holding the giveaway will actually do what they promise.
5. Mark Spoilers and NSFW
Make sure to mark your stuff or it may be removed.
No one wants to be spoiled. Therefore, always mark spoilers. Similarly mark NSFW, in case anyone is browsing in a public space or at work.
6. No linking to piracy
Don't share it here, there are other places to find it. Discussion of piracy is fine.
We don't want us moderators or the admins of lemmy.world to get in trouble for linking to piracy. Therefore, any link to piracy will be removed. Discussion of it is of course allowed.
Authorized Regular Threads
Related communities
PM a mod to add your own
Video games
Generic
- !gaming@Lemmy.world: Our sister community, focused on PC and console gaming. Meme are allowed.
- !photomode@feddit.uk: For all your screenshots needs, to share your love for games graphics.
- !vgmusic@lemmy.world: A community to share your love for video games music
Help and suggestions
By platform
By type
- !AutomationGames@lemmy.zip
- !Incremental_Games@incremental.social
- !LifeSimulation@lemmy.world
- !CityBuilders@sh.itjust.works
- !CozyGames@Lemmy.world
- !CRPG@lemmy.world
- !OtomeGames@ani.social
- !Shmups@lemmus.org
- !VisualNovels@ani.social
By games
- !Baldurs_Gate_3@lemmy.world
- !Cities_Skylines@lemmy.world
- !CassetteBeasts@Lemmy.world
- !Fallout@lemmy.world
- !FinalFantasyXIV@lemmy.world
- !Minecraft@Lemmy.world
- !NoMansSky@lemmy.world
- !Palia@Lemmy.world
- !Pokemon@lemm.ee
- !Skyrim@lemmy.world
- !StardewValley@lemm.ee
- !Subnautica2@Lemmy.world
- !WorkersAndResources@lemmy.world
Language specific
- !JeuxVideo@jlai.lu: French
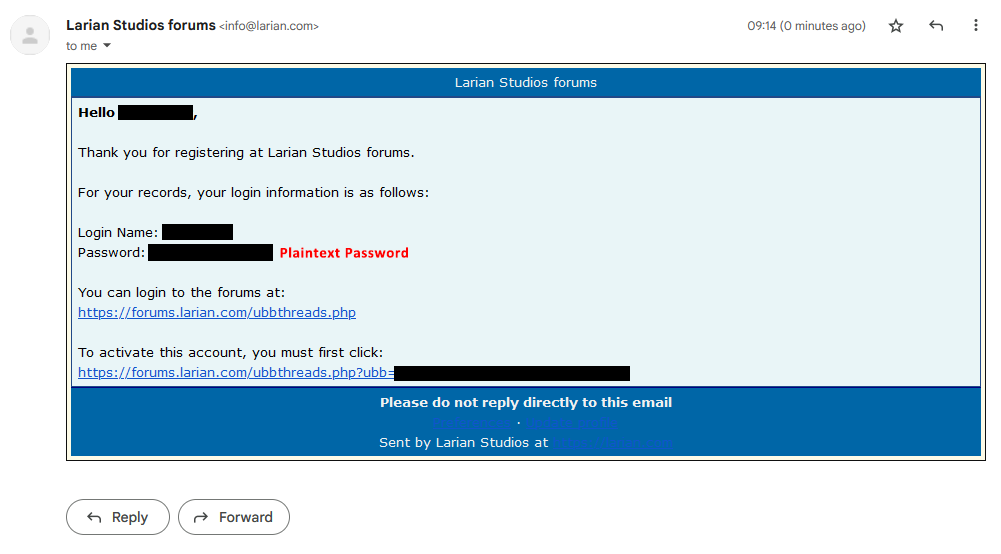
Just get a password manager already
https://bitwarden.com/
I want to suggest 1Password even though it’s not free (I used bitwarden for many years though). It has its own SSH agent which is a dream.
The only problem with their SSH agent is, if you store let’s say 6 keys and the server is set to accept a maximum of 5 keys before booting you, and the correct key happens to be key number 6, you can end up being IP banned.
This happened to me on my own server :P
That being said, my experience was using the very first GA release of their SSH Agent, so it’s possible the problem has been sorted by now.
BitWarden is awesome. Been using it since 2 of my colleagues went to work for them
How is this better than Firefox built-in password manager?
Firefox is extremely easy to get your password from behind the *** if it autofills. Requires physical access, but literally takes seconds. Right click the field, inspect and change the field type from password to text.
So if my passwords are behind fingerprint there's no problem?
On mobile I'm assuming. I personally don't know a way to bypass the fingerprint locks. And if you're also having Firefox create random difficult passwords, its significantly better than reusing the same one. So you're probably a much harder target than the majority of people. I'd have to double check but I think even on desktop if you have a master password for Firefox and don't just have logins auto filled you're probably good there too.
Thank you. I do use master password on everything. This does ease my mind a bit.
I just wanted to drop a reminder that both LastPass and Norton LifeLock have been hacked within the past year alone.
KeePass is a thing that exists and is fantastic.
I just want to drop a reminder (to you specifically) that you don't have to use a cloud-based password manager. Roll your own.
Can I discourage rolling your own password manager (like using a text doc or spreadsheet) and instead recommend what you hopefully meant, self-hosting your own password manager?
I don't know what you're trying to say. I think it was safe to assume Salty probably meant the local-based keepass or something like that?
I wouldn't have immediately gone to text doc or spreadsheet. those aren't password managers.
The only annoying part about the modern world is that you want to have that keepass file synchronized between devices, at which point you either go down the path of something like Synchthing (not mainstream user friendly) or you just end up asking yourself "fine, what cloud service do I trust to not go looking at my files?"
I always synced my database manually either directly over usb, or wifi (KDE Connect). I have to admit that it's not really user friendly, but once I got used to it, it's no problem at all.
And uploading it to any cloud service should be fine as long as it's encrypted with a strong password. But that kind of defeats the point of an offline password-manager in my opinion.
I have mine in a self hosted Nextcloud instance, best of both worlds
Good advice only for tech-savvy and people who are interested in self-hosting. There's so many things that can go wrong like improper backups and accidental networking problems.
And here's a reminder that trusting centralized service with high security access control is usually a bad idea.
I stay away from LastPass for the same reasons I stay away from TeamViewer. Security through obscurity on top of decoupling my security interests from others means other people being attacked is much less likely to cause me harm at the same time
Offline password managers like KeepassXC are a thing, plus self hosted remote storage like Nextcloud means you're not worried about any third party interference
Use KeePassXC and you can't get hacked
Well, you can. But you have to be PERSONALLY hacked. At which point you're at a level of risk equal to "will my house burn and my notebook full of passwords get lost?"
And at least for LastPass no passwords were compromised. Saying they "were hacked" and leaving the extent of the hack out implies something worse IMO, it's misleading. The safes themselves are E2E encrypted so they also don't have your password.
That said, my vote is to Bitwarden as it's open source and allows self hosting if you think you're a more reliable admin than they are. Open plus more choice is always better.
I'm just going to leave this here:
https://krebsonsecurity.com/2023/09/experts-fear-crooks-are-cracking-keys-stolen-in-lastpass-breach/
Just this month a link was made between $35 million in crypto being stolen and the 150 victims being LastPass users.
In 2022 Lastpass was compromised through a developer's laptop and had customer data like emails, names, addresses, partial credit cards, website urls, and most importantly vaults stolen last year, and given they're closed source, have no independent audits, and don't release white papers, we have no idea how good their encryption schemes actually are nor if they have any obvious vulnerabilities.
In 2021, users were warned their master passwords were compromised.
In 2020 they had an issue with the browser extension not using the Windows Data Protection API and just saving the master password to a local file.
What will 2024 bring for LastPass? They were hacked, and there's no reason to think they won't see more breaches of confidential customer information and even passwords in the future. This is a repeated pattern, and I'd better trust a post-it-note on my monitor for security than LastPass at this point.
This is true, but they have your encrypted vault, and all the technical data to make unlimited informed attempts at cracking it. If you used LastPass, you definitely need to be changing passwords for your critical services at a minimum.
One vote for 1Password here.
I literally trust them with my life. Agreed.
This is the correct answer.