view the rest of the comments
Games

Welcome to the largest gaming community on Lemmy! Discussion for all kinds of games. Video games, tabletop games, card games etc.
Rules
1. Submissions have to be related to games
Video games, tabletop, or otherwise. Posts not related to games will be deleted.
This community is focused on games, of all kinds. Any news item or discussion should be related to gaming in some way.
2. No bigotry or harassment, be civil
No bigotry, hardline stance. Try not to get too heated when entering into a discussion or debate.
We are here to talk and discuss about one of our passions, not fight or be exposed to hate. Posts or responses that are hateful will be deleted to keep the atmosphere good. If repeatedly violated, not only will the comment be deleted but a ban will be handed out as well. We judge each case individually.
3. No excessive self-promotion
Try to keep it to 10% self-promotion / 90% other stuff in your post history.
This is to prevent people from posting for the sole purpose of promoting their own website or social media account.
4. Stay on-topic; no memes, funny videos, giveaways, reposts, or low-effort posts
This community is mostly for discussion and news. Remember to search for the thing you're submitting before posting to see if it's already been posted.
We want to keep the quality of posts high. Therefore, memes, funny videos, low-effort posts and reposts are not allowed. We prohibit giveaways because we cannot be sure that the person holding the giveaway will actually do what they promise.
5. Mark Spoilers and NSFW
Make sure to mark your stuff or it may be removed.
No one wants to be spoiled. Therefore, always mark spoilers. Similarly mark NSFW, in case anyone is browsing in a public space or at work.
6. No linking to piracy
Don't share it here, there are other places to find it. Discussion of piracy is fine.
We don't want us moderators or the admins of lemmy.world to get in trouble for linking to piracy. Therefore, any link to piracy will be removed. Discussion of it is of course allowed.
Authorized Regular Threads
Related communities
PM a mod to add your own
Video games
Generic
- !gaming@Lemmy.world: Our sister community, focused on PC and console gaming. Meme are allowed.
- !photomode@feddit.uk: For all your screenshots needs, to share your love for games graphics.
- !vgmusic@lemmy.world: A community to share your love for video games music
Help and suggestions
By platform
By type
- !AutomationGames@lemmy.zip
- !Incremental_Games@incremental.social
- !LifeSimulation@lemmy.world
- !CityBuilders@sh.itjust.works
- !CozyGames@Lemmy.world
- !CRPG@lemmy.world
- !horror_games@piefed.world
- !OtomeGames@ani.social
- !Shmups@lemmus.org
- !space_games@piefed.world
- !strategy_games@piefed.world
- !turnbasedstrategy@piefed.world
- !tycoon@lemmy.world
- !VisualNovels@ani.social
By games
- !Baldurs_Gate_3@lemmy.world
- !Cities_Skylines@lemmy.world
- !CassetteBeasts@Lemmy.world
- !Fallout@lemmy.world
- !FinalFantasyXIV@lemmy.world
- !Minecraft@Lemmy.world
- !NoMansSky@lemmy.world
- !Palia@Lemmy.world
- !Pokemon@lemm.ee
- !Silksong@indie-ver.se
- !Skyrim@lemmy.world
- !StardewValley@lemm.ee
- !Subnautica2@Lemmy.world
- !WorkersAndResources@lemmy.world
Language specific
- !JeuxVideo@jlai.lu: French
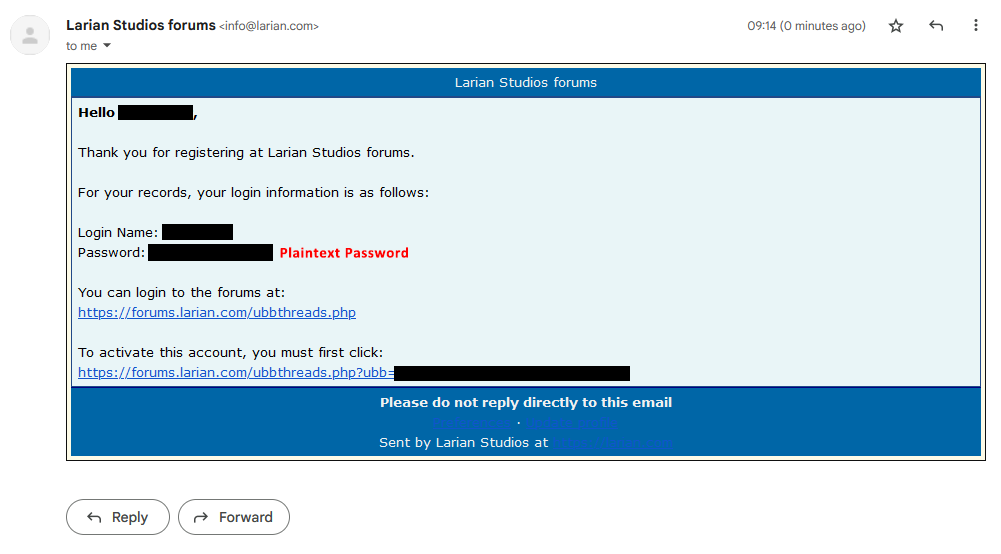
While sending your password in plaintext over email is very much a bad idea and a very bad practice, it doesn't mean they store your password in their database as plaintext.
Encrypted passwords are still an unacceptable way to store passwords. They should be hashed.
(and salted before hashing.)
And marinated in butter milk.
Peppered if you're feeling extra
Just because they send out the password does not mean it's not hashed. They could send the email before hashing.
You're correct and after reading more of the thread I saw OP say this was sent immediately after registering. I don't have reason to believe it is stirred in plaintext unless they're storing s copy of every email they send.
Would you accept "in a way that can be reversed"?
It's possible that this email is a result of forum user creation, so during that submission the plaintext password was available to send to the user. Then it would be hashed and stored.
I don't know why you'd give them any benefit of the doubt. They should have already killed that with this terrible security practice.
But yeah, sure, maybe this one giant, extremely visible lapse in security is the only one they have.
I'm just explaining how user authentication works for most web applications. The server will process your plaintext password when your account is created. It should then store that as a hashed string, but it can ALSO send out an email with that plaintext password to the user describing their account creation. This post does not identify that passwords are stored in plaintext, it just identifies that they email plaintext passwords which is poor security practice.
This particular poor security practice is very much like a roach. If you see one you have a bigger problem.
See, I can also repeat myself as though you didn't understand the first time.
Passwords shouldn't be stored at all though 🤷♂️
You mean plaintext passwords right? Ofcourse then need to store your (hashed)password!
The hash is not the password.
My bad! I just misunderstood >.<
If they stored the hashed password this thread wouldn't exist.
Point is, a hash isn't a password. giving the most you don't need tech knowledge analogy, it's like the passwords fingerprint.
The police station may keep your daughters fingerprint so that if they find a lost child they can recognize it is your daughter beyond any doubt. Your daughters fingerprints, is like a hash, your daughter is a password.
The police should not store your daughter... that's bad practice. The fingerprints are all they should store, and needless to say the fingerprints aren't your daughter, just as a hash isn't a password.