On March 10th, several days after Incognito Market was assumed to be shut down or no longer be processing transactions, the site posted a message to its homepage that reads as follows:
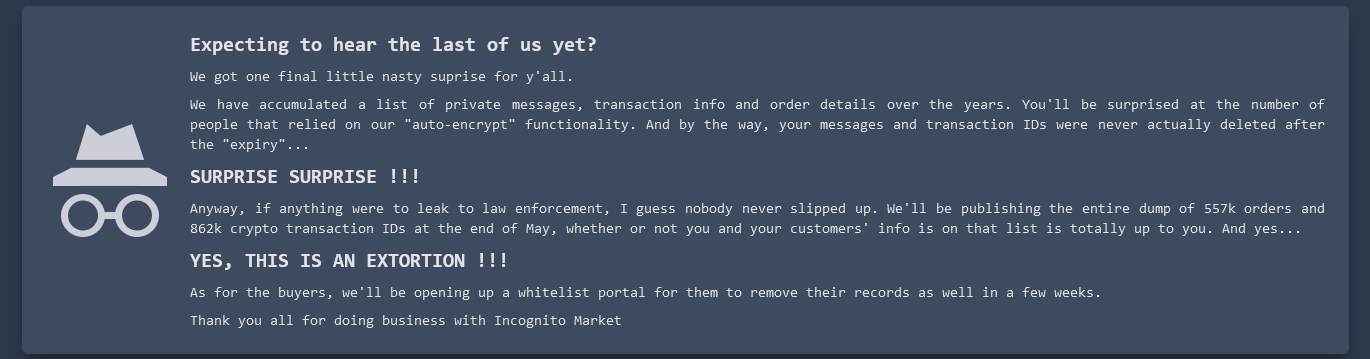
”Expecting to hear the last of us yet? We got one final little nasty suprise for y'all. We have accumulated a list of private messages, transaction info and order details over the years. You'll be surprised at the number of people that relied on our "auto-encrypt" functionality. And by the way, your messages and transaction IDs were never actually deleted after the "expiry"...”
”SURPRISE SURPRISE !!! Anyway, if anything were to leak to law enforcement, I guess nobody never slipped up. We'll be publishing the entire dump of 557k orders and 862k crypto transaction IDs at the end of May, whether or not you and your customers' info is on that list is totally up to you. And yes... YES, THIS IS AN EXTORTION !!! As for the buyers, we'll be opening up a whitelist portal for them to remove their records as well in a few weeks.”
”Thank you all for doing business with Incognito Market”
Exit scams are not uncommon on dark web markets, but this one is particularly large and openly threatening compared to most. Incognito Market requires the loading of cryptocurrency to a site-based wallet, which can then be used for in-house transactions only. All cryptocurrency on the site was seized from user’s wallets, estimated to be anywhere from $10 million to $75 million. After seizing the cryptocurrency wallets of all of the marketplace’s users, the site now openly explains that it will publish transactions and chat logs of users who refuse to pay an extortion fee. The fee ranges from $100 to $20,000, a volume based 5 tier buyer/seller classification.
Incognito Market also now has a Payment Status tab, which states ”you can see which vendors care about their customers below.” and lists the some of the market’s largest sellers. Sellers which have allegedly paid the extortion fee to not have their transaction records released are displayed in green, while those who have not yet paid are displayed in red.
Additionally, in a few weeks the site claims it will have a “whitelist portal” which would allow buyers to wipe their transactions and re-encrypt chat records.
Whoever is behind the website must be extremely, extremely confident in their anonymity, already working with government agencies, or both, because a bounty on this person is likely worth millions.
For christs sake:
Only ever explicitly discuss serious illegal activities in person, preferably outdoors and without any technology on you
Only coordinate meetings to discuss the above over an encrypted messaging method such as signal, and in this avoid specifics and keep this to an absolute minimum (metadata can also be incriminating, and phones out computers can be compromised)
If significant payment is involved, cash, barter or work trade are the only acceptable forms. Ever.
Don't be a fucking sucker
Any questions?
Signal is not secure, nor is Tor. Read "Surveillance Valley". That being said, you probably won't be visited by the cops over a buying a gram of something online.
I'm reading Surveillance Valley, and I'm not sure what you mean by "not secure"
The book states that Signal and Tor were developed by feds, meaning they're completely compromised. It's in the latter chapters.
The fact that tor was developed by feds (CIA agents actually use it in the field, too, IIRC) does not mean it's compromised. Its source code might be among the most audited ones around, including by well-known cryptographers. When the NSA put a backdoor in Dual_EC_DRBG, it was identified quickly and outside of shitty security appliances from RSA in corporate environments, very few projects actually ended up using it. I suspect such a thing would happen with tor.
SELinux is similar: developed by the NSA, but also audited to shit by countless security researcher eager to put their names on the map.
Also, the fact that all tor services that were taken down by LE thus far we know of were taken down through human error on the operator's side or active exploitation of software flaws in the service itself, combined with the Snowden leaks describing tor as a constant pain in their backside, also point towards the same conclusion.
While I don't think Tor is innately insecure or cryptographically compromised, it has been known for many years that a lot of its network nodes are operated by feds. Just due to the way Tor works, if you happen to control every node being used in a session, then you have full control and can de-anonymize users. Anyone can volunteer to act as a bridge/relay/exit node, and the feds obviously have the resources to pull off targeted attacks this way if they wanted to.
Any specific evidence of compromise? Governments have been known to fund and even directly develop tools later used against them.
I don't have the book checked out anymore, but once you get to the part about Ross ulbrecht, it's right around there. At bare minimum, you can force someone's identity. 0day exploits have also been given to the intelligence services first.
Thanks for the recommendation, I'll read that when I get a chance
What are better alternatives?
I have doubts about there being any.