view the rest of the comments
Selfhosted
A place to share alternatives to popular online services that can be self-hosted without giving up privacy or locking you into a service you don't control.
Rules:
-
Be civil: we're here to support and learn from one another. Insults won't be tolerated. Flame wars are frowned upon.
-
No spam posting.
-
Posts have to be centered around self-hosting. There are other communities for discussing hardware or home computing. If it's not obvious why your post topic revolves around selfhosting, please include details to make it clear.
-
Don't duplicate the full text of your blog or github here. Just post the link for folks to click.
-
Submission headline should match the article title (don’t cherry-pick information from the title to fit your agenda).
-
No trolling.
-
No low-effort posts. This is subjective and will largely be determined by the community member reports.
Resources:
- selfh.st Newsletter and index of selfhosted software and apps
- awesome-selfhosted software
- awesome-sysadmin resources
- Self-Hosted Podcast from Jupiter Broadcasting
Any issues on the community? Report it using the report flag.
Questions? DM the mods!
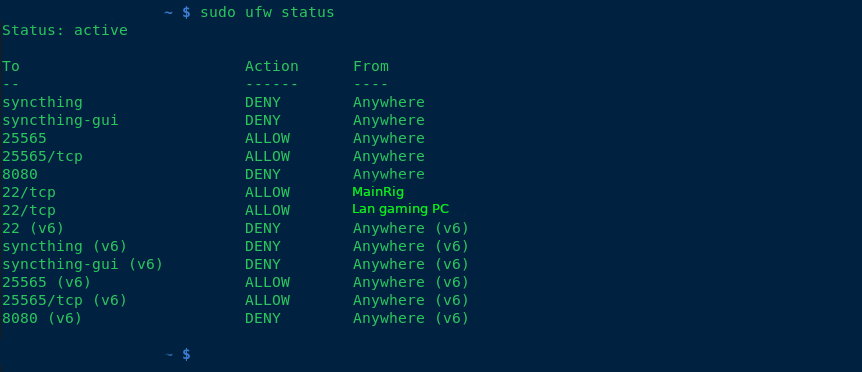
So the local machine doesn't really need the firewall; it definitely doesn't hurt, but your router should be covering this via port forwarding (ipv4) or just straight up firewall rules (ipv6).
You can basically go two routes to reasonable harden the system IMO. You can either just set up a user without administrative privileges and use something like a systemd system level service to start the server as that user and provide control over it from other users ... OR ... if you're really paranoid, use a virtual machine and forward the port from the host machine into the VM.
A lot of what you're doing is ... fine stuff to do, but it's not really going to help much (e.g. building system packages with hardening flags is good, but it only helps if those packages are actually part of the attack surface or rather what's exposed to the remote users in someway).
Your biggest risk is going to be plugins that aren't vetted doing bad things (and really only the VM or using the dedicated user account provides an insulation layer there -- the VM really only adds protection against privilege escalation which is pretty hard to pull off on a patched system).
My advice for most people:
For Minecraft in particular, to properly back things up on a busy server you need to disable auto save, manually force save, do the backup and then enable auto save again after your backup. Kopia can issue commands to talk to the server to do that, but you need a plugin that can react to those commands running on the server (or possibly to use the server console via stdin). Realistically though, that's overkill and you'll be just fine backing up the files exactly as they are periodically.
Kopia in particular will do well here because of its deduplication of baked up data + chunking algorithm that breaks up files. That has saved me a crazy amount of storage vs other solutions I've tried. Kopia level compression isn't needed because the Minecraft region files themselves are already highly compressed.