Leaked Docs Show What Phones Cellebrite Can (and Can’t) Unlock
The leaked April 2024 documents, obtained and verified by 404 Media, show Cellebrite could not unlock a large chunk of modern iPhones.
Cellebrite, the well-known mobile forensics company, was unable to unlock a sizable chunk of modern iPhones available on the market as of April 2024, according to leaked documents verified by 404 Media.
The documents, which also show what various Android handsets and operating system versions Cellebrite can access, provide granular insight into the very recent state of mobile forensic technology. Mobile forensics companies typically do not release details on what specific models their tools can or cannot penetrate, instead using vague terms in marketing materials. The documents obtained by 404 Media, which are given to customers but not published publicly, show how fluid and fast moving the success, or failure, of mobile forensic tools can be, and highlights the constant cat and mouse game between hardware and operating manufacturers like Apple and Google, and the hacking companies looking for vulnerabilities to exploit.
Analysis of the documents also comes after the FBI announced it had successfully gained access to the mobile phone used by Thomas Matthew Crooks, the suspected shooter in the attempted assassination of former President Donald Trump. The FBI has not released details on what brand of phone Crooks used, and it has not said how it was able to unlock his phone.
The documents are titled “Cellebrite iOS Support Matrix” and “Cellebrite Android Support Matrix” respectively. An anonymous source recently sent the full PDFs to 404 Media, who said they obtained them from a Cellebrite customer. GrapheneOS, a privacy and security focused Android-based operating system, previously published screenshots of the same documents online in May, but the material did not receive wider attention beyond the mobile forensics community.
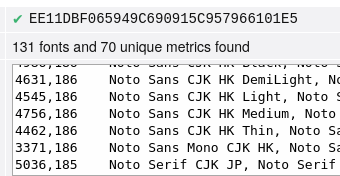
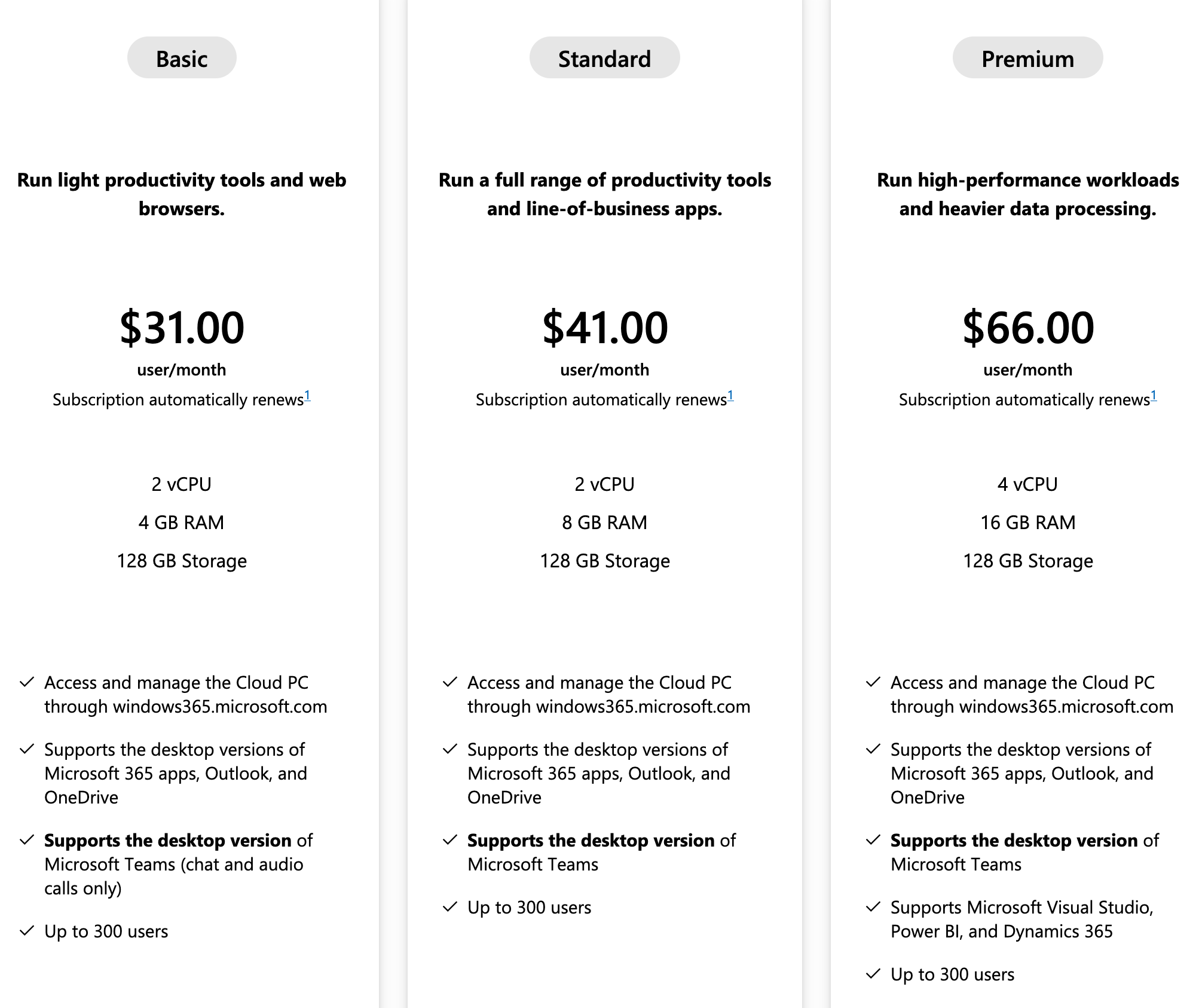
For all locked iPhones able to run 17.4 or newer, the Cellebrite document says “In Research,” meaning they cannot necessarily be unlocked with Cellebrite’s tools. For previous iterations of iOS 17, stretching from 17.1 to 17.3.1, Cellebrite says it does support the iPhone XR and iPhone 11 series. Specifically, the document says Cellebrite recently added support to those models for its Supersonic BF [brute force] capability, which claims to gain access to phones quickly. But for the iPhone 12 and up running those operating systems, Cellebrite says support is “Coming soon.”
A SECTION OF THE IOS DOCUMENT. IMAGE: 404 MEDIA.
The iPhone 11 was released in 2019. The iPhone 12 was launched the following year. In other words, Cellebrite was only able to unlock iPhones running the penultimate version of iOS that were released nearly five years ago.
The most recent version of iOS in April 2024 was 17.4.1, which was released in March 2024. Apple then released 17.5.1 in May. According to Apple’s own publicly released data from June, the vast majority of iPhone users have upgraded to iOS 17, with the operating system being installed on 77 percent of all iPhones, and 87 percent of iPhones introduced in the last four years. The data does not break what percentage of those users are on each iteration of iOS 17, though.
Cellebrite offers a variety of mobile forensics tools. That includes the UFED, a hardware device that can extract data from a physically connected mobile phone. The UFED is a common sight in police departments across the country and world, and is sometimes used outside of law enforcement too. Cellebrite also sells Cellebrite Premium, a service that either gives the client’s UFED more capabilities, is handled in Cellebrite’s own cloud, or comes as an “offline turnkey solution,” according to a video on Cellebrite’s website.
That video says that Cellebrite Premium is capable of obtaining the passcode for “nearly all of today’s mobile devices, including the latest iOS and Android versions.”
That claim does not appear to be reflected in the leaked documents, which show that, as of April, Cellebrite could not access from locked iOS phones running 17.4.
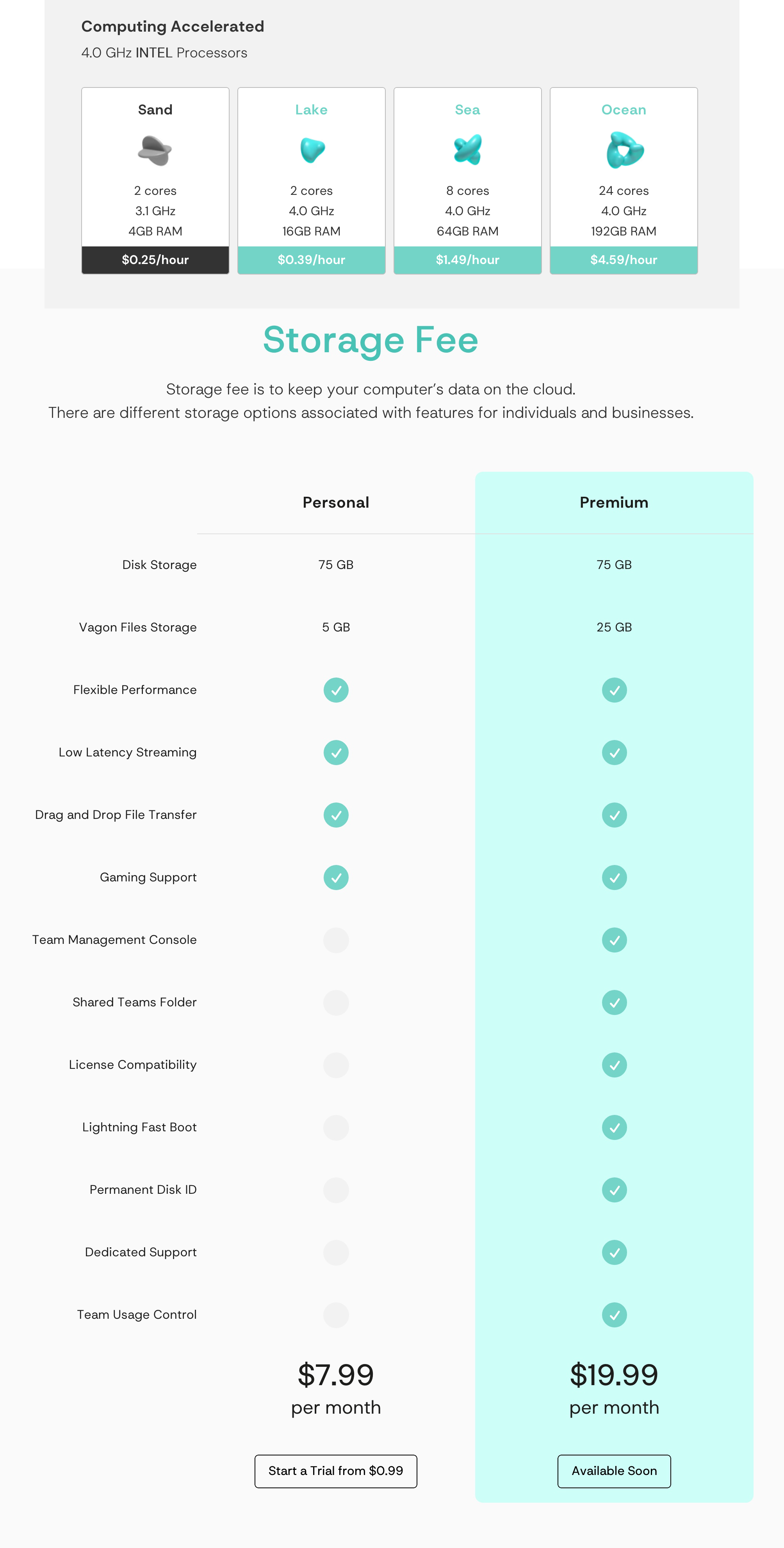
The second document shows that Cellebrite does not have blanket coverage of locked Android devices either, although it covers most of those listed. Cellebrite cannot, for example, brute force a Google Pixel 6, 7, or 8 that has been turned off to get the users’ data, according to the document. The most recent version of Android at the time of the Cellebrite documents was Android 14, released October 2023. The Pixel 6 was released in 2021.
A SECTION OF THE ANDROID DOCUMENT. IMAGE: 404 MEDIA.
Cellebrite confirmed the authenticity of the documents in an emailed statement to 404 Media. “Similar to any other software company, the documents are designed to help our customers understand Cellebrite’s technology capabilities as they conduct ethical, legally sanctioned investigations—bound by the confines of a search warrant or an owner’s consent to search. The reason we do not openly advertise our updates is so that bad actors are not privy to information that could further their criminal activity,” Victor Ryan Cooper, senior director of corporate communications and content at Cellebrite, wrote.
“Cellebrite does not sell to countries sanctioned by the U.S., EU, UK or Israeli governments or those on the Financial Action Task Force (FATF) blacklist. We only work with and pursue customers who we believe will act lawfully and not in a manner incompatible with privacy rights or human rights,” the email added. In 2021 Al Jazeera and Haaretz reported that a paramilitary force in Bangladesh was trained to use Cellebrite’s technology.
Cellebrite is not the only mobile forensics company targeting iOS devices. Grayshift makes a product called the GrayKey, which originally was focused on iOS devices before expanding to Android phones too. It is not clear what the GrayKey’s current capabilities are. Magnet Forensics, which merged with Grayshift in 2023, did not immediately respond to a request for comment.
Cellebrite’s Android-focused document also explicitly mentions GrapheneOS in two tables. As well as being an operating system that the privacy-conscious might use, 404 Media has spoken to multiple people in the underground industry selling secure phones to drug traffickers who said some of their clients have moved to using GrapheneOS in recent years.
Daniel Micay, founder of GrapheneOS, told 404 Media that GrapheneOS joined a Discord server whose members include law enforcement officials and which is dedicated to discussions around mobile forensics. “We joined and they approved us, with our official GrapheneOS account, but it seems some cops got really mad and got a mod to ban us even though we didn't post anything off topic or do anything bad,” Micay said.
There is intense secrecy around the community of mobile forensics experts that discuss the latest unlocking tricks and shortcomings with their peers. In 2018 at Motherboard, I reported that law enforcement officials were trying to hide their emails about phone unlocking tools. At the time, I was receiving leaks of emails and documents from inside mobile forensics groups. In an attempt to obtain more information, I sent public records requests for more emails.
“Just a heads up, my department received two public records request[s] from a Joseph Cox at Motherboard.com requesting 2 years of my emails,” a law enforcement official wrote in one email to other members. I learned of this through a subsequent leak of that email. (404 Media continues to receive leaks, including a recent set of screenshots from a mobile forensics Discord group).
Google did not respond to a request for comment. Apple declined to comment.